Previous Projects
The following research was performed with the Energy Efficient Circuits & Systems Group at MIT:
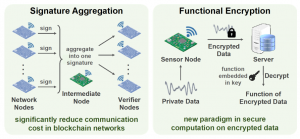
Low-Power BLS12-381 Elliptic Curve Pairing Crypto-Processor (2020-21)
|
with Prof. Anantha P. Chandrakasan
We present the first BLS12-381 elliptic curve pairing crypto-processor for low-power embedded IoT applications. Efficient finite-field arithmetic and algorithm-architecture co-optimizations together enable two orders of magnitude energy savings. We also implement several countermeasures against timing and power side-channel attacks. Our crypto-processor is programmable to provide the flexibility to accelerate various elliptic curve cryptography and pairing-based cryptography protocols such as signature aggregation and functional encryption. |
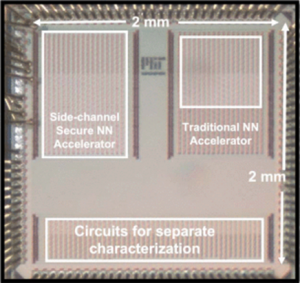
Side-Channel-Resilient Neural Network Hardware Accelerator (2020-21)
|
with Saurav Maji, Dr. Samuel H. Fuller and Prof. Anantha P. Chandrakasan
We demonstrate the first ASIC implementation of a neural network hardware accelerator with improved resilience against power and electromagnetic side-channel attacks for the security of both model parameters and inputs, suitable for resource-constrained IoT applications. Side-channel-secure threshold implementation masking-based design methodology is supplemented with algorithmic and architectural innovations to achieve neural network computations with reduced area/energy overheads and without comprising throughput. The accelerator also secures model parameters through encryption and protects inputs against horizontal power analysis attacks. Related Publications: ISSCC 2022, JSSC 2023 Press Mentions: MIT News, ACM News, Indian Express, SciTech Daily |
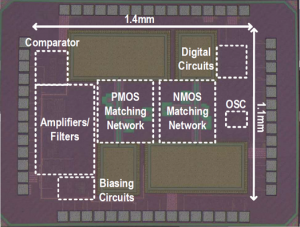
Secure THz Wake-Up Receiver (2020-21)
|
with Eunseok Lee, Muhammad Ibrahim Wasiq Khan, Xibi Chen, Nathan Monroe, Prof. Rabia T. Yazicigil, Prof. Ruonan Han and Prof. Anantha P. Chandrakasan
We demonstrate the first secure THz wake-up receiver with integrated cryptographic authentication to prevent denial-of-sleep and battery drainage attacks. The chip implements a THz frontend based on a pair of dual-antenna-feed, pseudo-differential CMOS THz detectors and an amplifier-filter-comparator chain, along with a built-in low-power authentication block that Related Publications: CICC 2023, JSSC 2024 Press Mentions: MIT News, IEEE Spectrum, Interesting Engineering, TechExplorist, All About Circuits, Electronics For You |
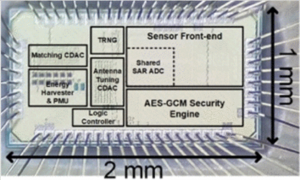
Secure Wireless Batteryless Implantable System-on-Chip (2020)
|
with Mohamed R. Abdelhamid, Unsoo Ha, Prof. Fadel Adib and Prof. Anantha P. Chandrakasan
We present a wireless, batteryless and secure implantable system-on-a-chip with integrated strain sensing. The system implements a fully reconfigurable implantable rectenna, a highly efficient high-resolution high-dynamic-range strain sensing front-end, an ultra-low-power AES security engine, a chaos map TRNG and over-the-air closed-loop wireless programming. Related Publications: CICC 2022, OJSSCS 2023 |
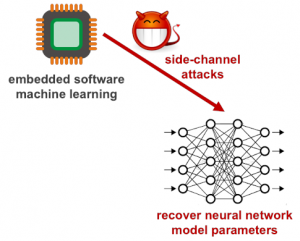
Side-Channel Analysis of Embedded Neural Network Implementations (2019-20)
 |
with Saurav Maji and Prof. Anantha P. Chandrakasan
We study the side-channel vulnerabilities of embedded neural network implementations by recovering their model parameters as well as inputs using timing-based information leakage and simple power analysis side-channel attacks. We demonstrate our attacks on popular micro-controller platforms over networks of different precision such as floating point, fixed point and binary networks, and also propose countermeasures against timing attacks. Related Publications: IoTJ 2021 |
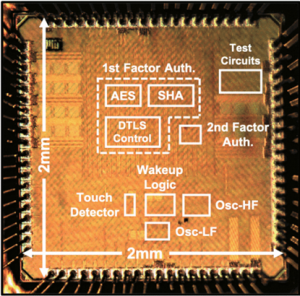
Dual-Factor Authentication for Securing Biomedical Devices (2019-20)
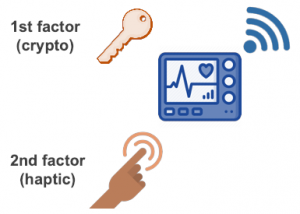
|
with Saurav Maji, Dr. Samuel H. Fuller, Mohamed R. Abdelhamid, Phillip M. Nadeau, Prof. Rabia T. Yazicigil and Prof. Anantha P. Chandrakasan
We present a dual-factor authentication protocol and its low-power implementation for securing medical devices. The protocol incorporates traditional cryptographic first-factor authentication using DTLS-PSK followed by the user’s touch-based voluntary second-factor authentication for enhanced security. The chip implements a low-power compact always-on wake-up timer, touch-based wake-up circuitry and a hardware accelerated dual-factor authentication unit. Our test chip is coupled with commercial Bluetooth Low Energy transceiver, DC-DC converter, touch sensor and coin cell battery to demonstrate standalone implantable operation and also tested using in-vitro measurement setup. Related Publications: CICC 2020, ISLPED 2020 Design Contest, SSCMag 2020, CBMS 2021 |
Efficient Post-Quantum TLS using Identity-Based Key Exchange from Lattices (2019)
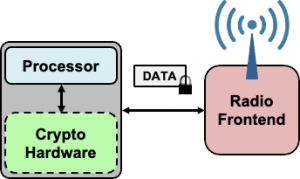 |
with Prof. Anantha P. Chandrakasan
We build on the well-known lattice-based DLP-IBE scheme to construct an ID-based certificate-less authenticated key exchange for post-quantum TLS handshakes. We also propose concrete parameters for the underlying lattice computations and provide detailed implementation results to analyze the associated energy savings. Related Publications: ICC 2020 |
Accelerating Post-Quantum Cryptography using a TLS Crypto-Processor (2019)
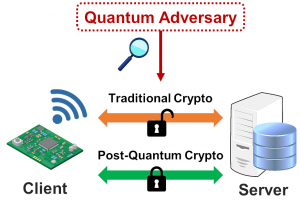 |
with Siddharth Das and Prof. Anantha P. Chandrakasan
We re-purpose the AES, SHA and ECC cryptographic accelerators in an energy-efficient pre-quantum TLS crypto-processor to implement post-quantum key encapsulation schemes SIKE, Kyber, Frodo and ThreeBears and signature scheme SPHINCS+ through software-hardware co-design with a RISC-V processor. Related Publications: ISCAS 2020 |
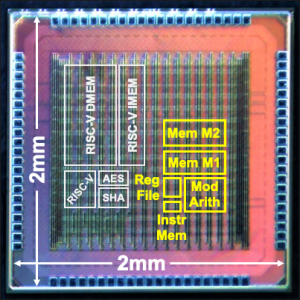
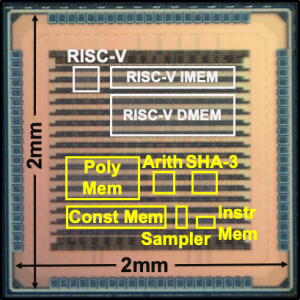
Quantum-Secure Configurable Lattice Crypto-Processor (2018-19)

|
with Abhishek Pathak, Tenzin S. Ukyab and Prof. Anantha P. Chandrakasan
We present a lattice cryptography processor with configurable parameters which enables energy savings and system area reduction through architectural optimizations. The crypto-processor can be programmed with custom instructions for polynomial arithmetic and sampling, and it is coupled with a low-power RISC-V micro-processor to accelerate various lattice-based cryptography protocols. All key building blocks of the chip are constant-time and secure against timing and simple power analysis side-channel attacks. This is the first ASIC implementation which demonstrates multiple NIST post-quantum standardization candidates such as NewHope, Kyber, Frodo, qTesla and Dilithium. Related Publications: ISSCC 2019, TCHES 2019, ISLPED 2020 Design Contest Press Mentions: MIT News, IEEE Spectrum, TechXplore, Science Blog, PQCzoo Patent: US11416638B2 |
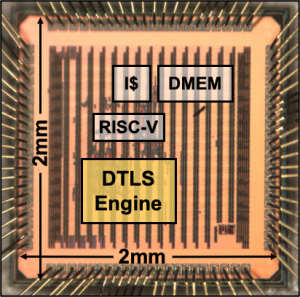
Energy-Efficient DTLS Cryptographic Engine for IoT Security (2017-18)
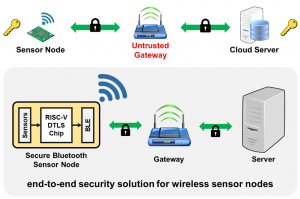
|
with Andrew Wright, Chiraag Juvekar, Madeleine Waller, Prof. Arvind and Prof. Anantha P. Chandrakasan
We present the first full-hardware implementation of DTLS with configurable cryptographic accelerators and a dedicated protocol state machine for energy savings and reduced memory usage. A low-power RISC-V processor is used to exercise the flexibility of the cryptographic accelerators to demonstrate security applications. A secure IoT node is designed with the test chip which collects data from a temperature sensor and an accelerometer, encrypts it, and then transmits it over a DTLS-secured channel through Bluetooth Low Energy (BLE). Related Publications: ISSCC 2018, JSSC 2019 Press Mentions: MIT News, Financial Times, TechRepublic, ZDNet, TechExplorist, Engadget, BitDefender Blog, WikiChip Patent: US11070362B2 |
Energy-Efficient Datagram Transport Layer Security for IoT (2016-17)
 |
with Chiraag Juvekar, Dr. Samuel H. Fuller and Prof. Anantha P. Chandrakasan
We profile the energy costs of DTLS 1.3 using experimental models for cryptographic computations and RF communications. Based on this analysis, we present eeDTLS, a low-energy variant of DTLS, which provides the same security strength but employs a combination of packet size reduction and optimized handshake computation for energy savings. Related Publications: GLOBECOM 2017 |
Power Side-Channel Attack on Embedded Software Encryption (2015)
 |
with Lisa Ho and Skanda Koppula
We demonstrate the extraction of secret key from Arduino implementing AES-128. We repeatedly measure the chip’s power consumption during encryption and correlate with a Hamming weight power model for all possible key bytes to ultimately extract the 128-bit key. Related Publications: Technical Report |