Abstract
In this work, the development and use of a framework to emulate timing side channel attacks and detect
vulnerabilities in the embedded systems is discussed. The framework developed is used to test a simple string-matching
function and the ReLU activation function for tinyML and secure them against timing side channel attacks. The CMSIS NN
library is also tested for possible side channel vulnerabilities.
INTRODUCTION
A side-channel attack is a security exploit that aims to gather information from or influence the program execution
of a system by measuring indirect effects of the system or its hardware – rather than targeting the program or its code
directly. It exploits different parameters like timing, power, EM field etc. of a device and predicts the actual functionality
of the program it is running.
The outcome of this project is a flexible framework for characterizing security critical components of embedded
systems for timing side channel vulnerabilities. The system has an embedded component that is injected in the code base
to make necessary measurements or control the inputs and an analysis component which analyzes the data collected in
python. The framework enables characterizing the timing of code components to check for vulnerabilities. This can be
done with inputs chosen by the user fed into the system or by passively recording the timing and relevant measurements of
code that runs as part of a larger system. The user can check various combinations of inputs which they think may be used
for a side channel attack and check if the system has timing variations that can be exploited. This information can be used
to iteratively fix any vulnerabilities.
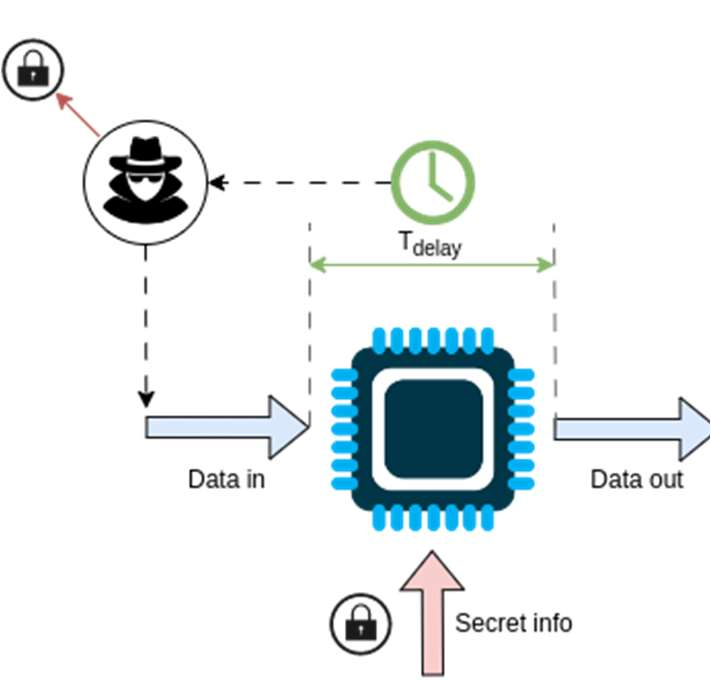
Fig-1: Illustration of timing side-channel attack
Here, a framework has been used to execute timing attack on a string-matching function embedded in ARM Cortex M4
microcontroller detecting the key, followed by designing a string-matching algorithm resistant to such attacks. The
framework has been used to emulate timing side-channel attack on a tinyML neural network implemented in Cortex-
M4 using CMSIS NN library and attempt improvements.Often these vulnerabilities may not be visible from the high-
level structure of the code and are caused by behavior at the assembly level due to compiler optimizations or hardware
behaviors like pipeline and cache flushes. Therefore, characterizing the system in a minimally invasive manner is
important in verifying the security of the final product rather than relying on the security of the algorithms themselves.
TEST FRAMEWORK
A versatile framework was developed for characterizing timing and emulating possible timing attacks on embedded
systems. It was developed to be flexible and portable between platforms and use-cases. It can work in two configurations –
an active configuration and a passive observer configuration.
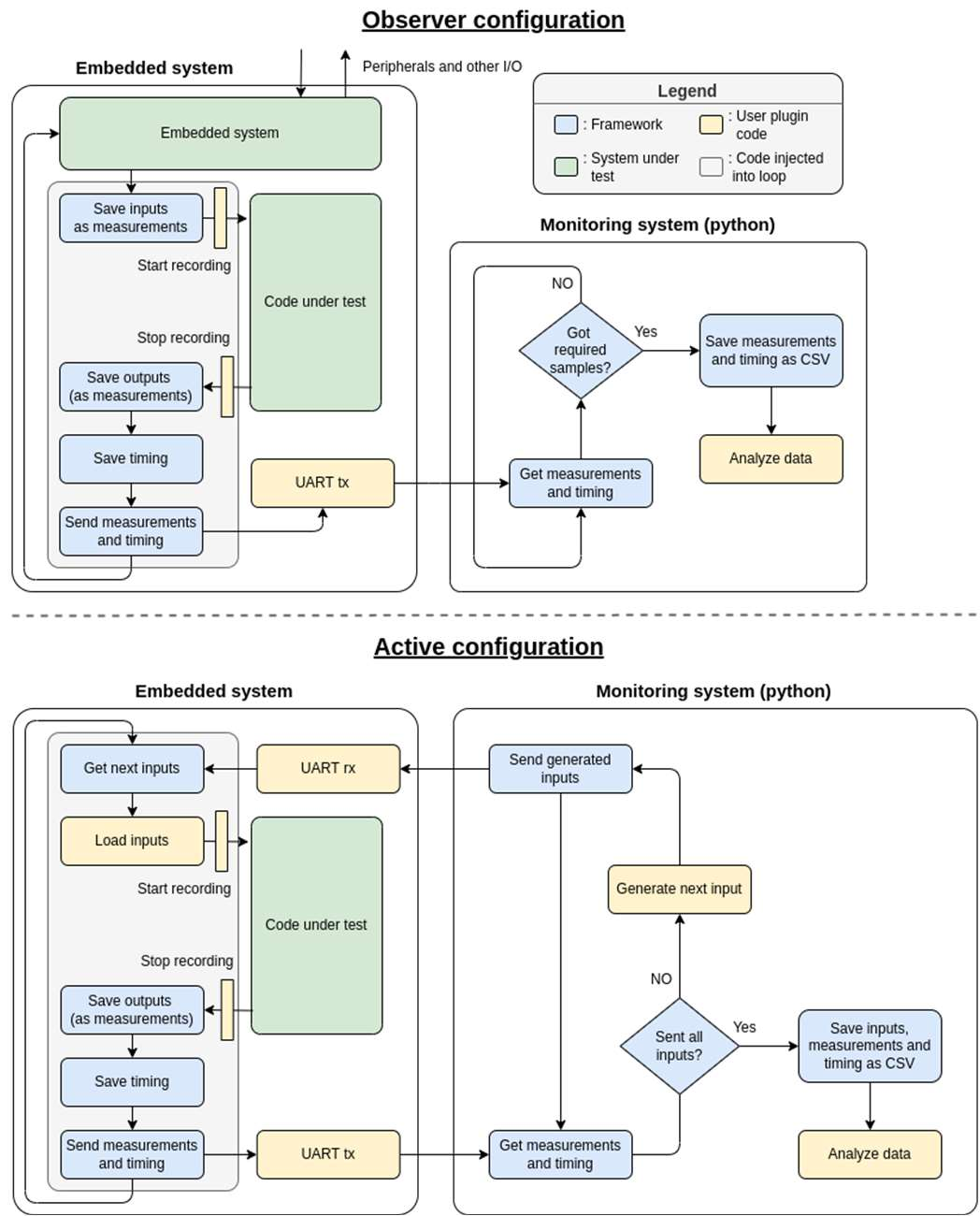
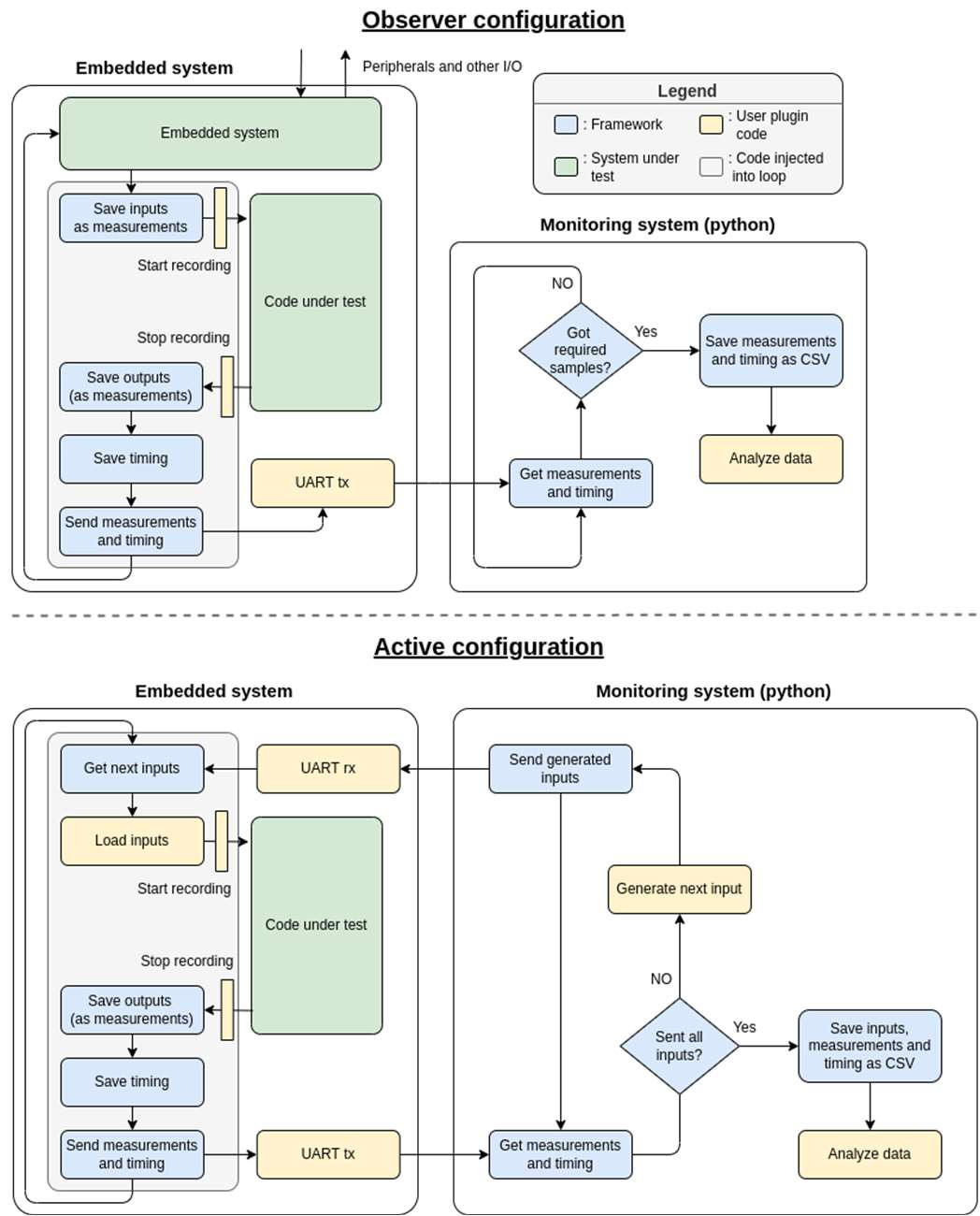
Fig-2: Flowcharts of two configurations of the framework
The core functionality of the framework involves two-way UART communication between the embedded system and a
python-based testbench which can feed inputs to the system and gets the timing information and any useful internal
measurements in return. This can be used to find correlations between inputs or hidden information and timing. Further,
once an attack strategy is formed, the user can write the attack algorithm which would feed inputs to the system and gets the
timing and modifies the next guess in response. The framework can transfer either an 8-bit, 16-bit or 32-bit int
array or a string as input and gets either an 8-bit, 16-bit or 32- bit int array or string as the measurement along with the
number of cycles taken to run the code under observation. The data type and number of inputs/measurements can be
configured at run-time.
The user needs to handle platform-specific details like UART transmission and reception and timer functionality.
The UART transmission function needs to be passed as a callback function and the UART reception function needs to
call the parse function of the framework when it receives a string. The user needs to implement the timing system and
functions which when called will start or stop the timer and then return the timer value. These need to be done for every
new platform being tested. On the analyzer side, the user canfeed the inputs to the embedded system and get timing and
measurements corresponding to the input or can log thereceived measurements and timings in the observer mode.
ATTACK ON STRING MATCHING FUNCTION
The framework has been used to execute timing attack on a string-matching function (check_pass1) embedded in M4.
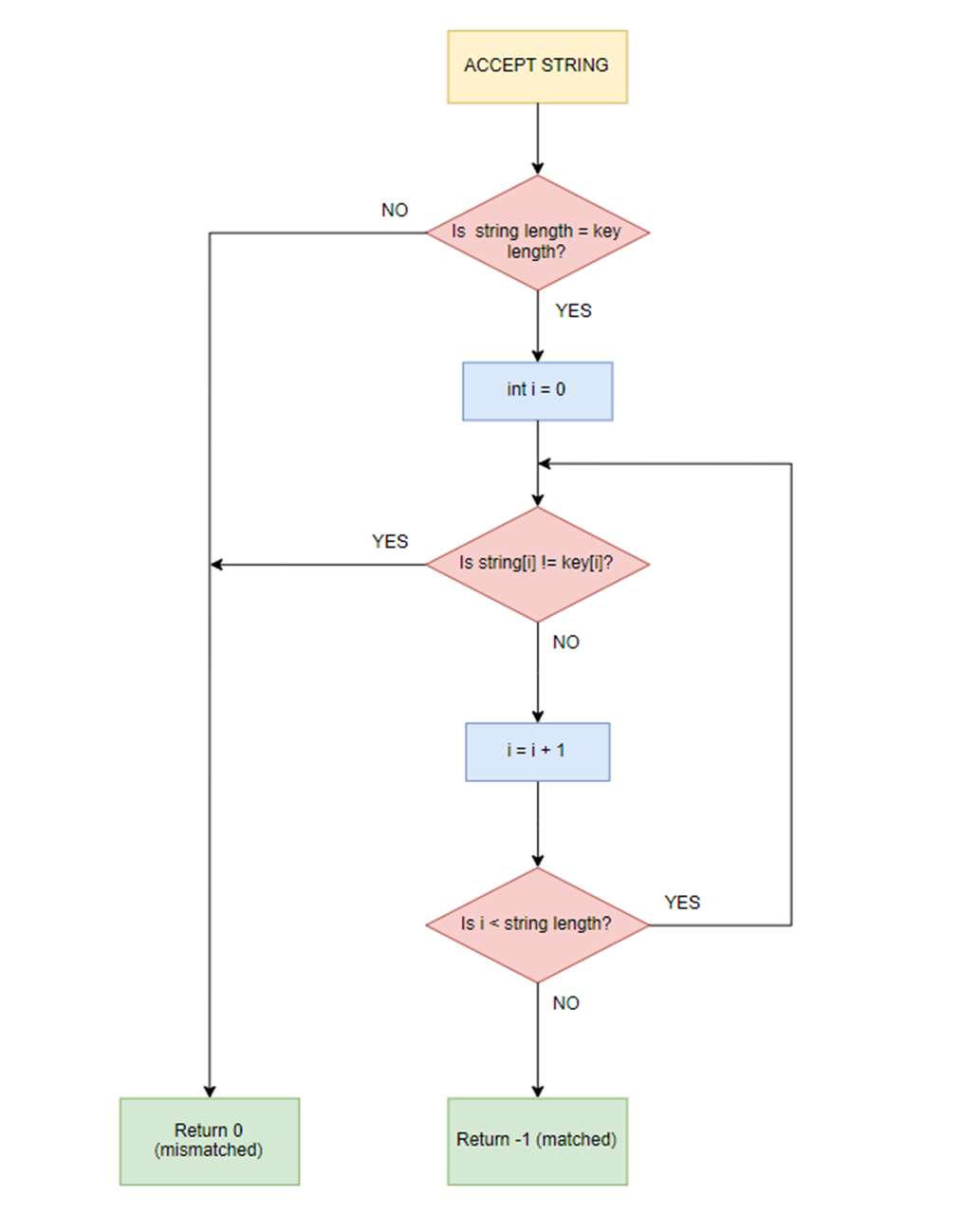
Fig-3: Flowchart of check_pass1 function
mismatch and then checks characters one by one. Each time the match occurs, it branched to the next process. This creates
the timing difference, which can be captured from the power waveform or EMC spectrum. Here, to emulate the attack,
another program in the same microcontroller has been introduced that provides the timing delay (in terms of clock
cycles) or active high pulse in a GPIO pin as feedback. The timing attack algorithm is implemented in Python to
communicate with microcontroller via UART. It sends a password to the microcontroller and analyzes the timing
feedback received. Based on that it first calculates the length of the key and then the characters one-by-one.
First it sends a single character string and checks the timing. Then it sends two character strings and checks the
timing. If the timing is same as the first, it sends three- character strings. And it continues until the timing changes.
The length of the string at that instant marks the key length. Then, it iterates through all the characters in 1st position
and checks timing. When timing changes, the character at that instant is the character at that position in the key. Then it
repeats the same for all the characters and when the match occurs for the final character, it breaks and gives the key.
The timing pattern observed throughout the attack on implementation of check_pass1() function is shown below.
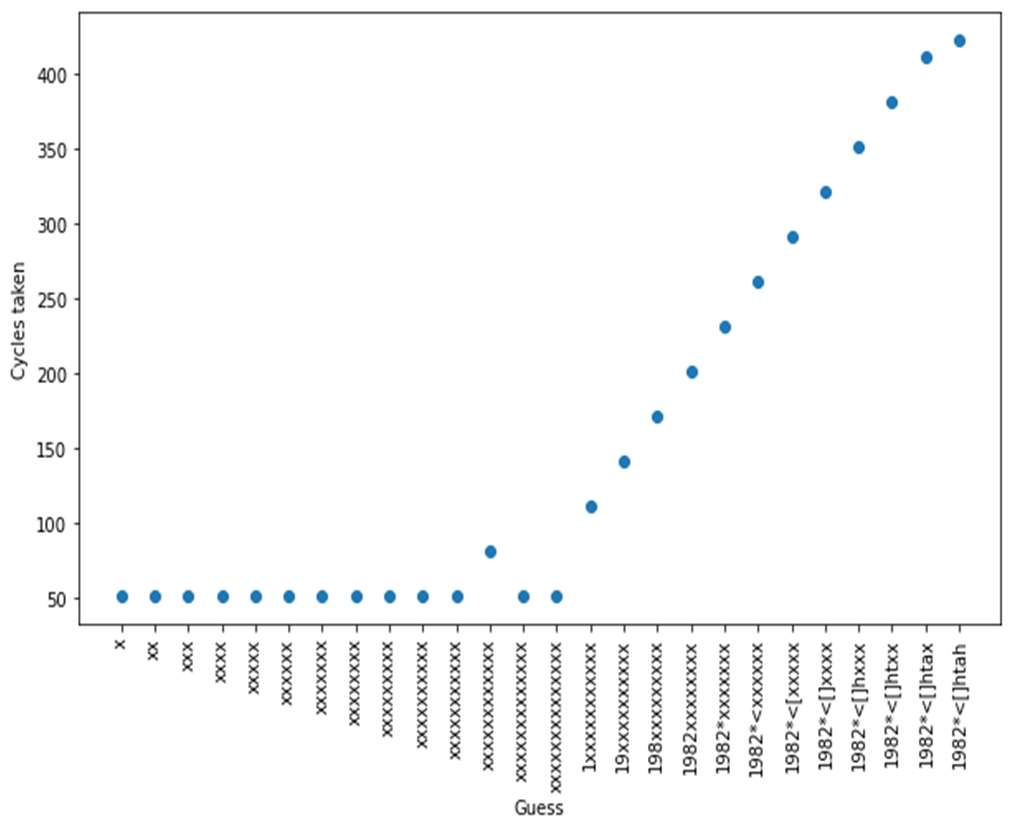
Fig-4: Timing pattern of check_pass1 function
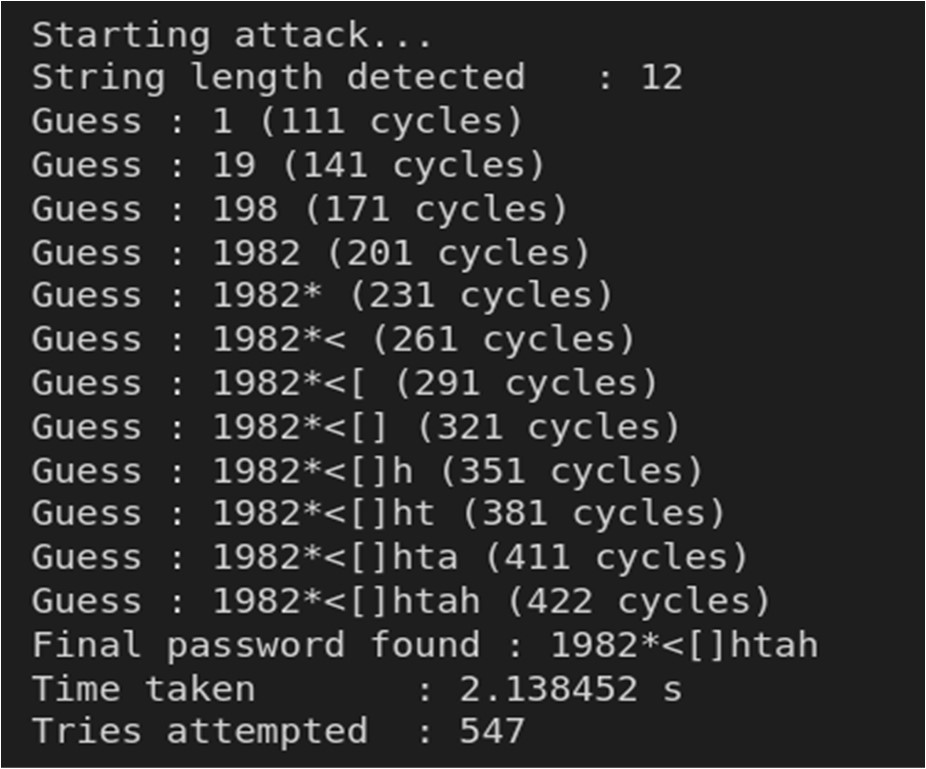
Fig-5: Outcome of the timing attack on check_pass1 function
However, to enhance the safety of password matching algorithm and making it resistant to the timing attack, the
algorithm has been progressively developed in three stages. In check_pass2() function, the length check function is
avoided and ‘flag’ variable is introduced. Inside the character checking loop, the ‘if-else’ conditional branching has been
equalized to generate minimal timing difference on match.
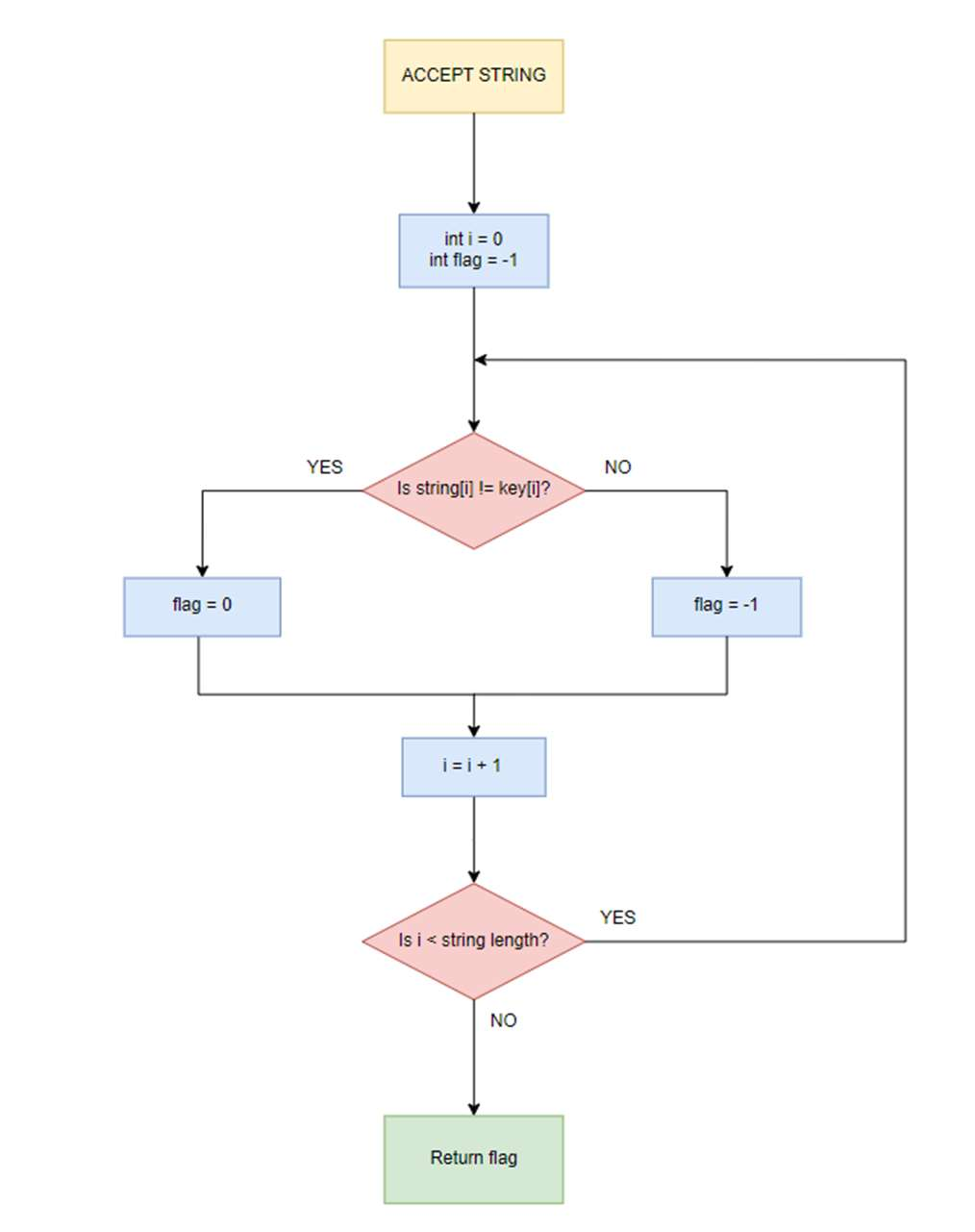
Fig-6: Flowchart of check_pass2 function
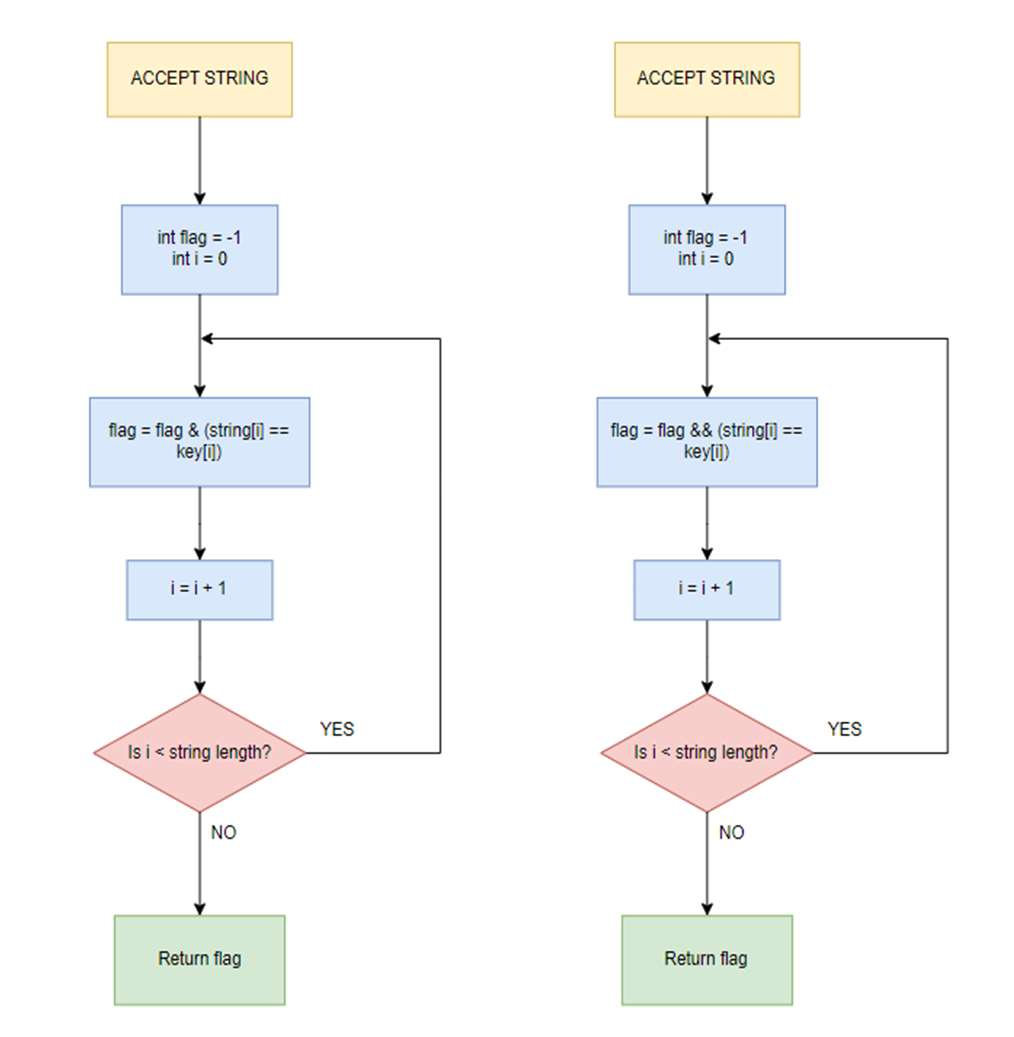
Fig-7: Flowcharts of check_pass3 (left) and check_pass4 (right) functions
In check_pass3() function, all the branching has been omitted. Here, the flag is set by the logical AND operation
with matching condition. In check_pass4(), the flag is set by the bitwise AND operation with matching condition.
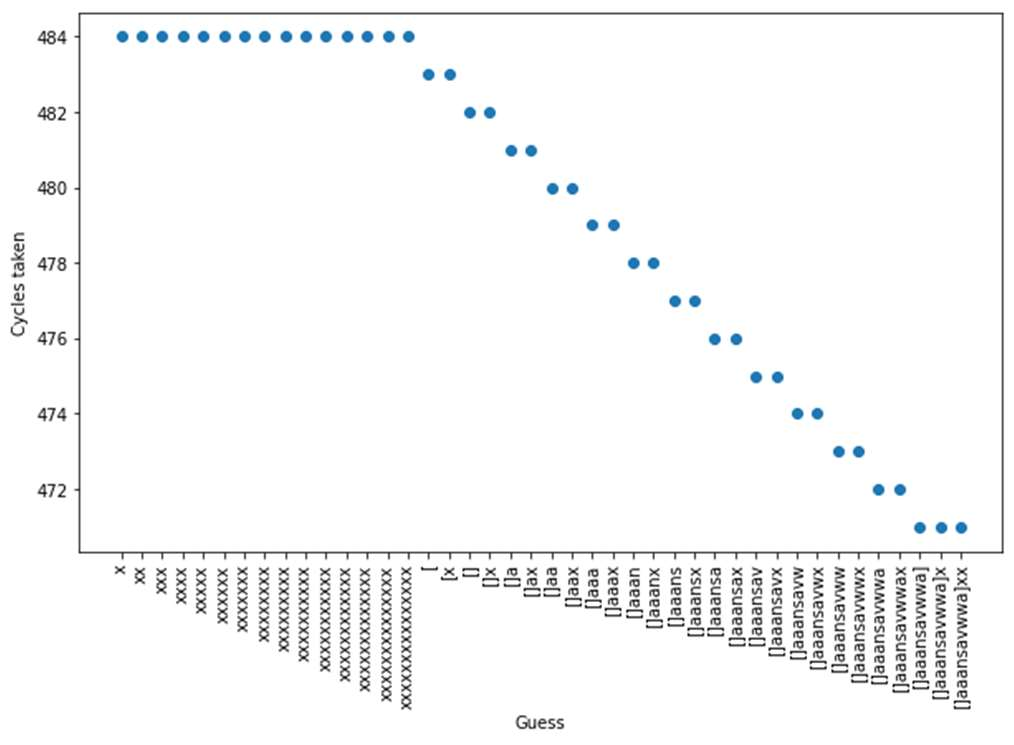
Fig-8: Timing pattern of check_pass2 function
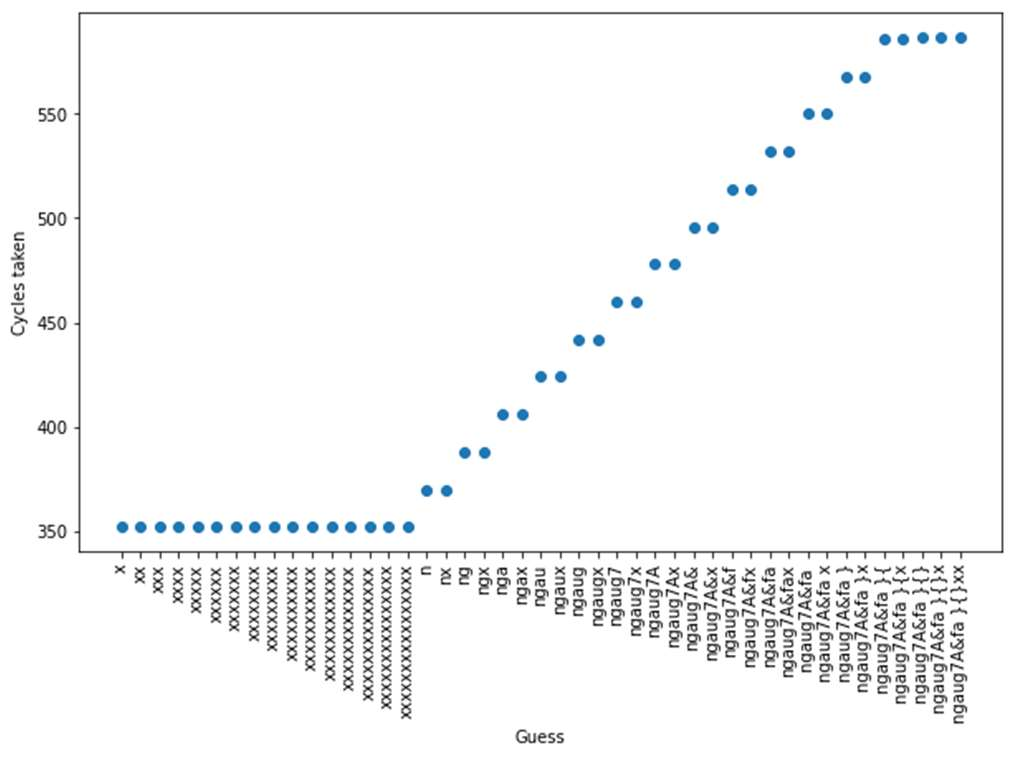
Fig-9: Timing pattern of check_pass3 function
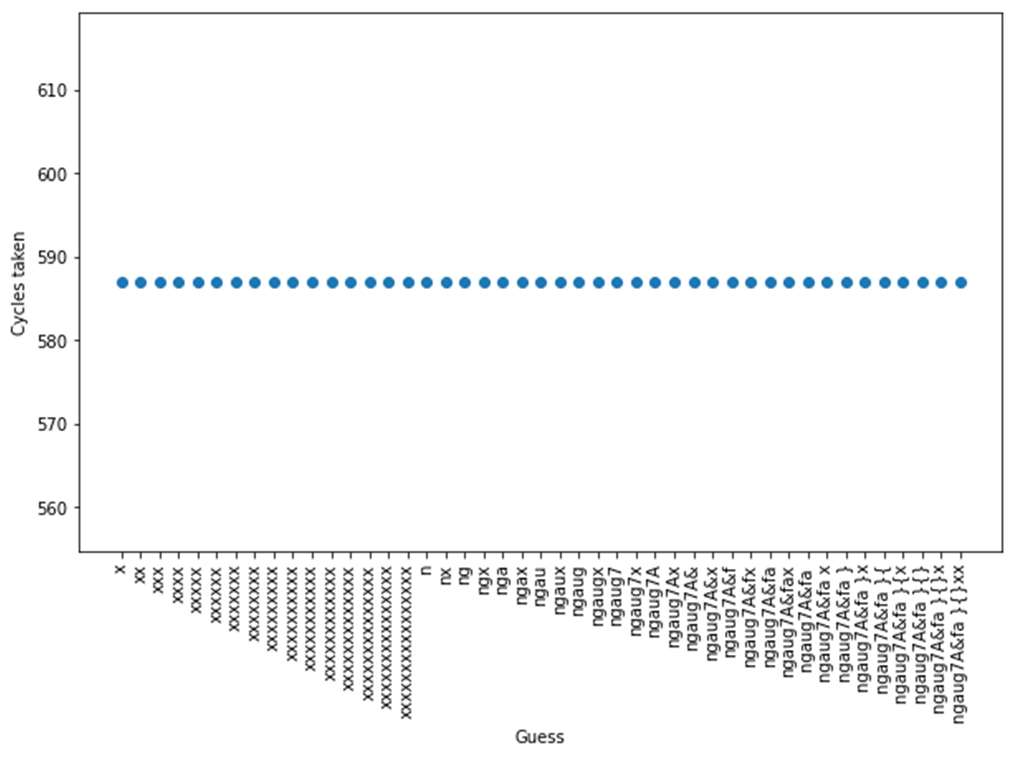
Fig-10: Timing pattern of check_pass4 function
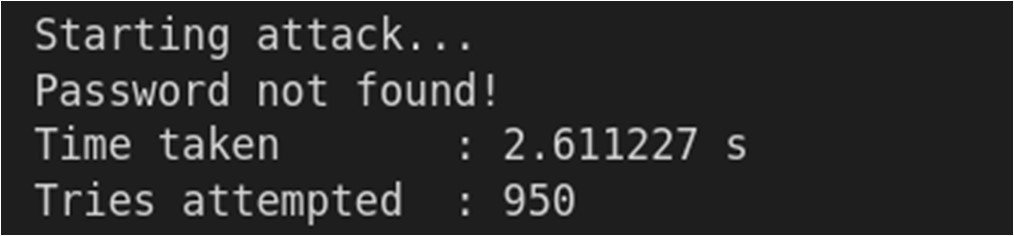
Fig-11: Outcome of the timing attack on check_pass4 function
The check_pass2() function has some timing differences, but lower than that of check_pass1() function. This improves
gradually and check_pass4() functions comes with no timing differences at all. Thus, check_pass4() string matching
algorithm is resistant to the timing attack.
The framework is also used to check CMSIS NN library for known side-channel vulnerabilities in the neural network
implementations. It is found that the use of DSP masking instructions and look-up tables in the ReLU and sigmoid/tanh
activation functions respectively prevent most common side channel attacks on neural networks. However, the ARM
Cortex M0 and M3 do not use the DSP instructions and the ReLU activation function on these processors can be
subjected to well-known side-channel attack techniques to extract model information.
The tinyML networks are analyzed using well-known vulnerabilities in the ReLU function. ReLU function is a
simple activation function which is 0 if the input is less than 0 and returns the input itself if it is greater than 0. The
common implementation of ReLU is implemented using if- else branching and has different timing if the input is less than
or greater than 0. When part of a network, this can be used to find the “input crossover point” for each input which is the
input for which the ReLU output switches from the “off” to “on” state. This can be used to find the weights and biases in
the input layer of the network.
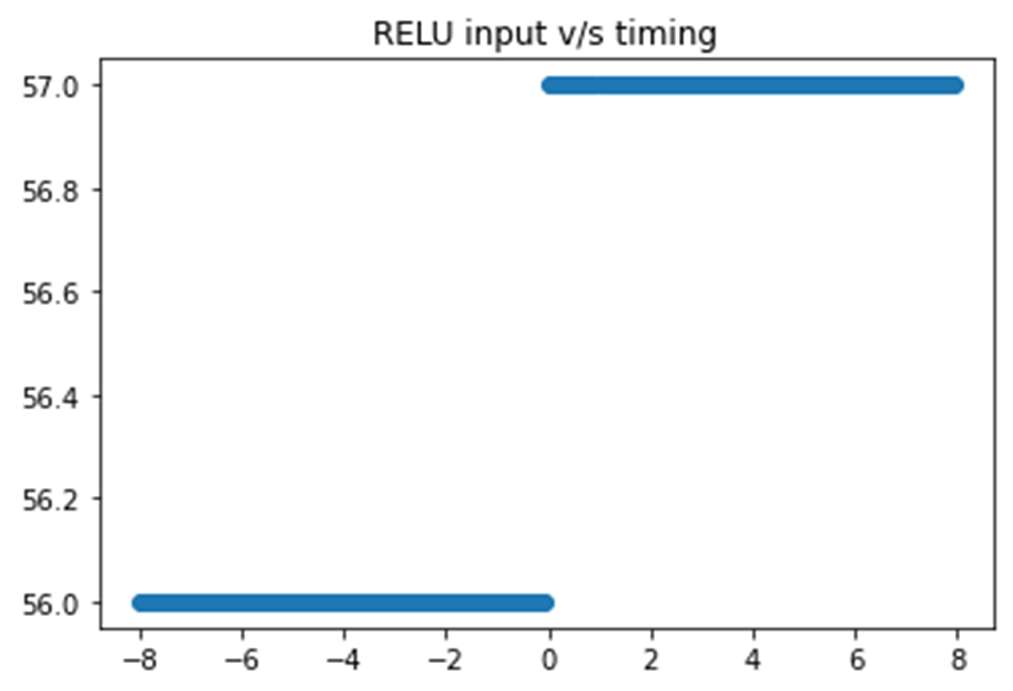
Fig-12: Timing of network v/s inputs to ReLU
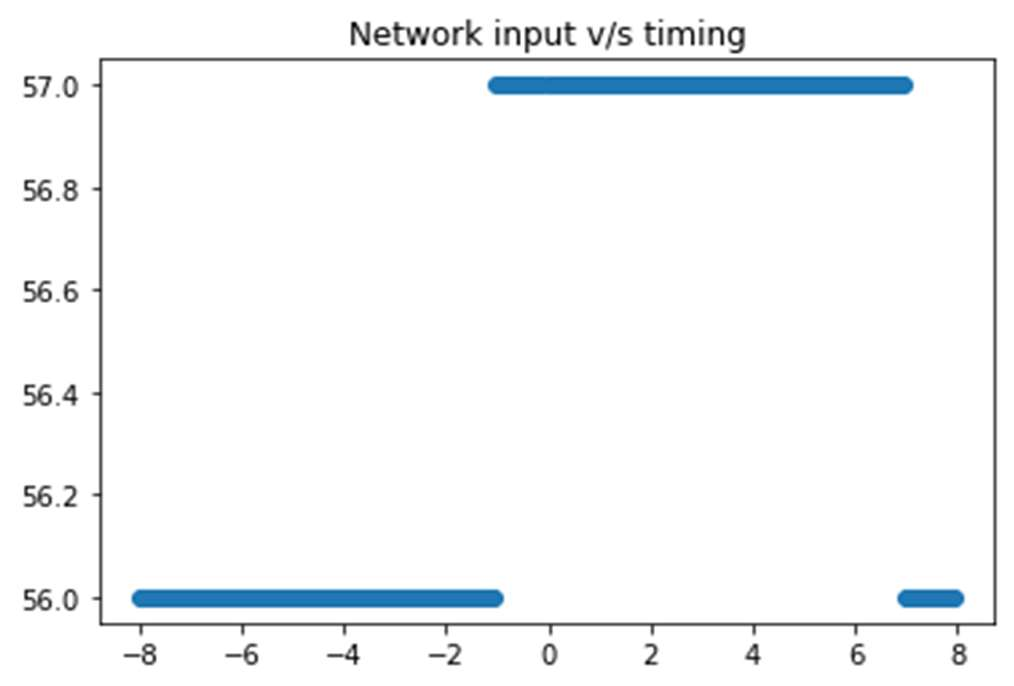
Fig-13: Timing v/s single input (ipk) to the network (all other inputs zeroed)
In the above figures, the y-axis represents the timing (inns). Probing and varying different inputs (ipk) to the network(making all other inputs zero), the zero cross-over input will
vary, that provides significant timing information to reverse engineer the ratio of weights and biases corresponding to the
neurons. To fix this vulnerability, the implementation of if- else branching was changed to a mask-based implementation
using shifting and bitwise and operations. This leads to a timing characteristic which is independent of the input,
denying the possibility for a timing –based attack.
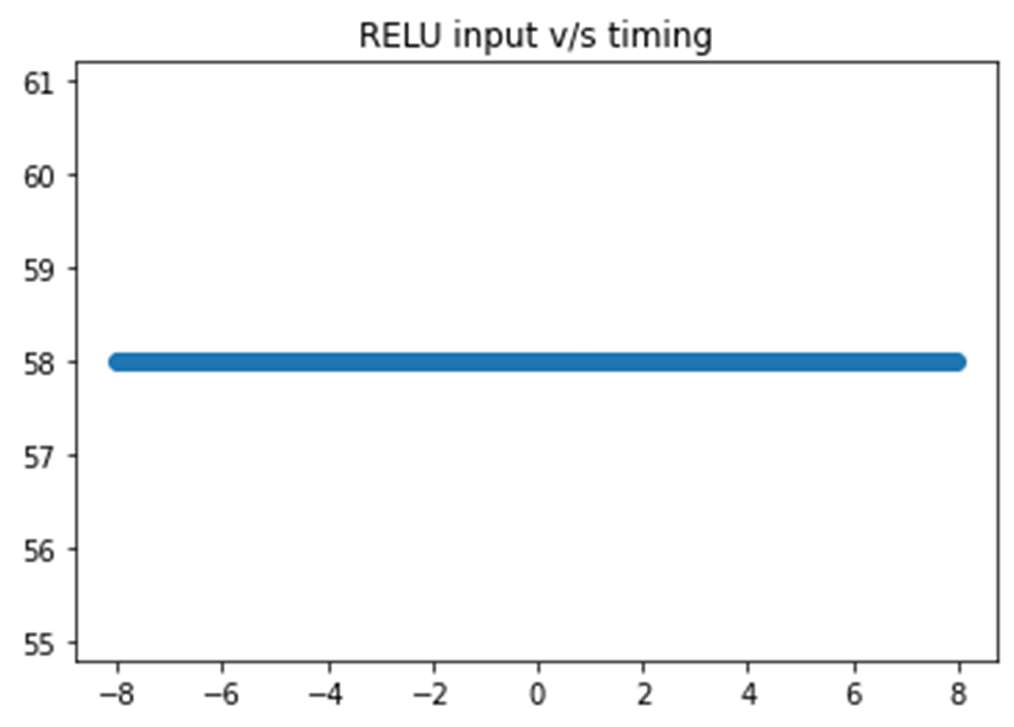
Fig-14: Timing v/s input of secured RELU function
\
The above result is displayed for all kinds of inputs, resulting in no timing vulnerabilities at all. This ensures the
newly designed ReLU function is resistant to timing attacks.
CONCLUSION
A framework has been designed for testing timing side channel vulnerabilities on embedded systems. It has been
used to test a known vulnerability in a string-matching algorithm and develop an attack strategy. The design has
been iteratively improved to create a secure system. Further, the vulnerability of tinyML implementations via the ReLU
activation function has been tested and used to develop a secure ReLU implementation. The CMSIS NN library for
implementing neural networks in embedded systems has also been tested against common vulnerabilities to find that it is
secure against most known attacks.
REFERENCES
[1]Saurav Maji, Utsav Banerjee and Anantha P. Chandrakasan. Leaky Nets: Recovering Embedded Neural Network Models and Inputs
through Simple Power and Timing Side-Channels – Attacks and Defenses. IEEE Internet of Things Journal. 2021
[2]Lejla Batina, Shivam Bhasin, Dirmanto Jap and Stjepan Picek. CSI NN: Reverse Engineering of Neural Network Architectures Through
Electromagnetic Side Channel. 28th USENIX Security Symposium.2019
Code:Timing side channel attack on TinyML
Demo: Timing side channel attack on TinyML
Recent Comments