Objectives
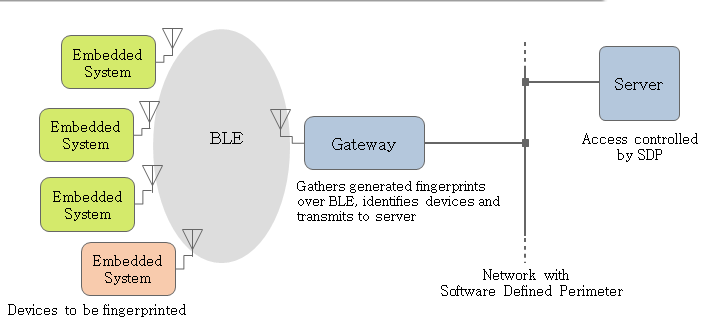
The objective of the project is to generate a unique signature for an embedded system and to set up a secure network with Software Defined Perimeter (SDP) so that only data from identified nodes reach the server.
Scope
- Identification of features that form a device fingerprint
- Generation of fingerprint of a device requires identification of unique hardware features that could be exploited. There are two requirements for a feature to be useful as a fingerprint:
- Identified parameter is required to be unique for an individual device and distinct from an identical device
- The measured parameter should be consistent for a device over a specified range of operating conditions
- Generation of fingerprint of a device requires identification of unique hardware features that could be exploited. There are two requirements for a feature to be useful as a fingerprint:
- After extraction of signature features, they are transmitted over BLE link to a gateway.
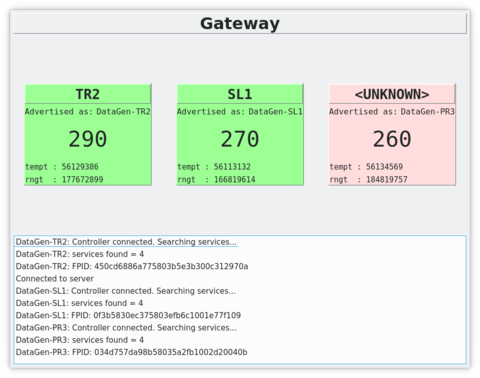
- The acquired features are matched at the gateway to distinctly identify the transmitting node
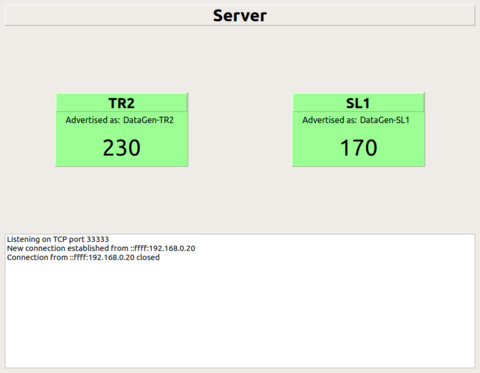
- The gateway is connected to a server that is behind a drop-all firewall using port-knocking (SDP)
- The implementation ensures transmission of simulated sensor data from identified nodes to the server and filters out data from non-identified devices
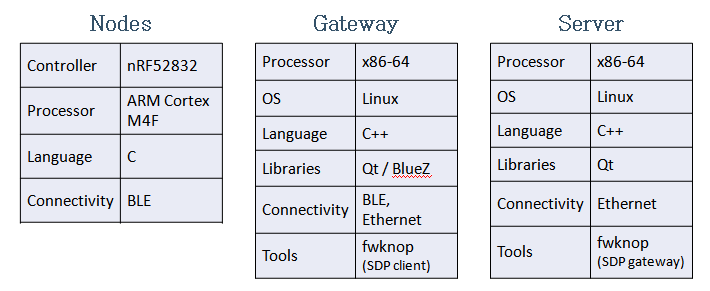
Platform Configurations
The platform configurations used for end node, gateway and server are shown here.
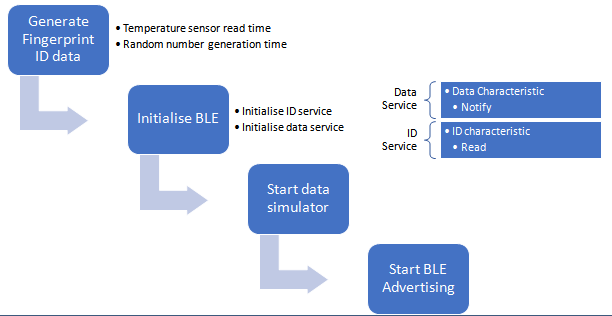
End Node Configuration
The signature generated at the embedded device is transmitted over Bluetooth Low Energy (BLE) to the gateway machine. Two different services have been enabled at the device as follows.
- ID Service – consists of ID characteristic (fingerprint data) sent to the gateway with READ property
- Data Service – consists of data characteristic (simulated data) sent to the gateway with NOTIFY property
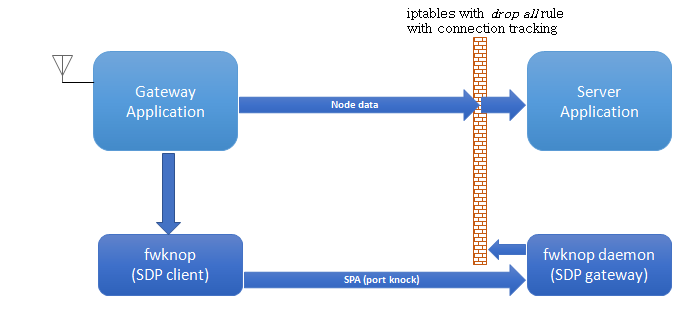
Gateway and Server Configurations
Gateway and Server applications are configured for Software Defined Perimeter (SDP) client and gateway roles respectively (controller is not implemented). FwKnOp (Firwall Knock Operator) application is used for these functions. The server firewall is configured with drop all rules and connection tracking setup of iptables. A port knock (Single Packet Authorisation) from SDP client to gateway opens specific preconfigured port for establishing connectivity for a short time window. This establishes continuous connectivity from gateway application to server as the connection tracking feature of the firewall keeps established connections active after the short time window.
Measurements and Results
Programmable Peripheral Interconnect
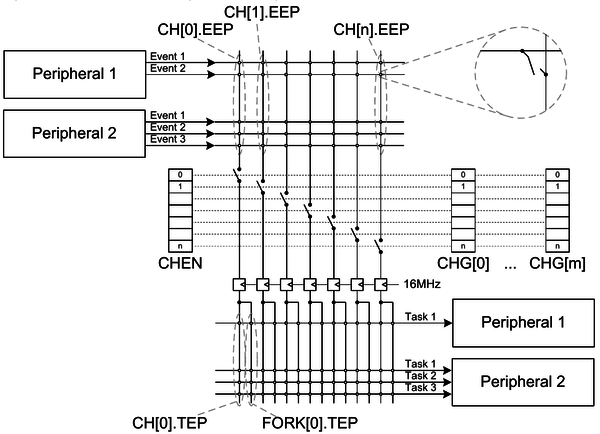
The nRF52832 microcontroller features a Programmable peripheral
interconnect (PPI) that enables peripherals to interact autonomously with each other using tasks and events independent of the CPU. The PPI allows precise synchronization between peripherals when real-time application constraints exist and eliminates the need for CPU activity to implement behaviour which can be predefined using PPI. The PPI provides a mechanism to automatically trigger a task in one peripheral as a result of an event occurring in another peripheral. A task is connected to an event through a PPI channel. The PPI channel is composed of three end point registers, one EEP and two TEPs. A peripheral task is connected to a TEP using the address of the task register associated with the task. Similarly, a peripheral event is connected to an EEP using the address of the event register associated with the event. The second task end point allows to trigger a second task in addition to the first one.
Precise time measurement using PPI
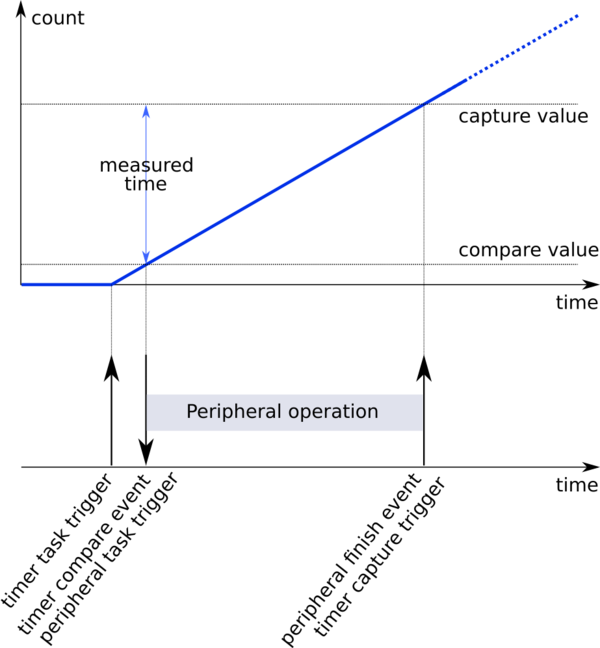
The general method adopted for measurement of time elapsed between events
(such as time taken for measurement of one temperature sample) is shown above. Two PPI channels are utilised. The first channel connects the compare event of a timer with the start task of the process to be measured. The second channel connects the finished event of the process to the capture task of the same timer. The compare value for the timer is initialised to a small value. When the timer is triggered, it generates an event when the count value reaches the set compare value. This triggers the start of the process to be measured. Once the process finishes, it’s event causes the timer’s value to be captured. The difference in the capture value and the compare value gives the number of timer counts (and therefore the time) spent in execution of the process. This process is repeated sufficient number of times to accumulate the time values to generate a signature that is characteristic of a particular device/board.
Among the five features investigated, two (Temperature sensor read time and random number generation time) were identified to be suitable candidates. Unique signature extraction from embedded device (nRF52832 Nordic controller) has yielded the following results.
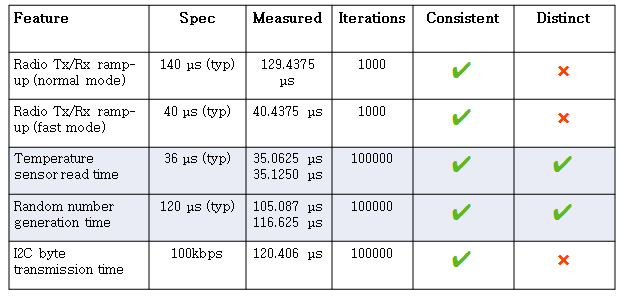
Temperature sensor read time
The temperature read time taken for six different devices and taken for 100,000 cycles each have been accumulated. The results are as follows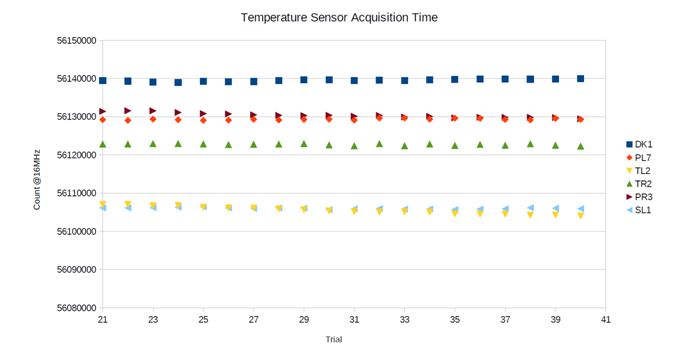
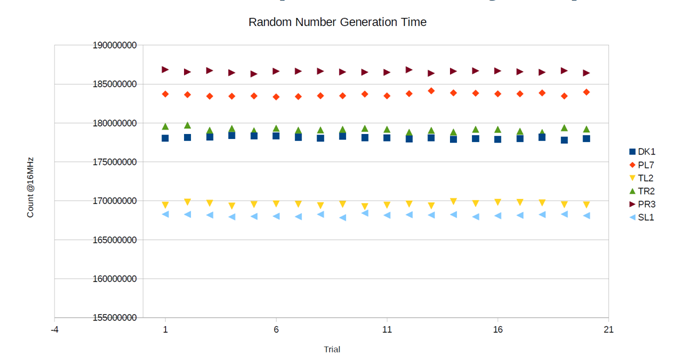
Random number generation time
The random number generation time taken for six different devices and taken for 100,000 cycles each have been accumulated. The results are as follows
Software Implementation
As described in section 3 above, our implementation has three elements – an embedded system node that generates some data, a gateway machine and a server that is the end-point for the data. Software developed for the three roles are available on Github:
Findings and Insights for Future Work
A proof-of-concept implementation for exploiting existing features/peripherals of an embedded system for uniquely identifying a device has been demonstrated successfully. However, more features need to be identified for better accuracy and resilience against variations. Further, more sophisticated feature matching techniques need to be implemented to have resilience against variability in measured features over time and their dependence on environmental factors such as temperature. Improvement in obtained results for unique identification can be achieved by approaching the scenario as a multi-class classification problem.
Gallery

Recent Comments