Power Side-channel Attack on software implemented AES using chipwhisperer NANO
Abstract
In this project, we demonstrated the extraction of an AES secret key from flash memory of target side of
chipwhisperer NANO board. It is done by capturing the power traces of the plain text with every possible key, and
correlating these traces with the hamming weight of s-box output. And, ultimately extracted 128-bit key used during
AES. This work presents introduction to side channel attack, chipwhisperer nano board, chipwhisperer software, attack
on AES, correlation power analysis (CPA), and results of theattack.
Keywords—Side-channel attack, Chip-whisperer NANO, AES, CPA
INTRODUCTION
From information security perspective, protecting sensitive data requires utilizing algorithms which resist theoretical
attacks. Encryption systems have become essential for security-critical applications such as military, government,
and banking systems. These encryption systems are designed to scramble the data and keep them safe from the
hackers. However, implementation of such systems is indeed difficult than theory itself. And, treating an
algorithm in a purely mathematical fashion or in other words, abstracting away from its physical implementation
(both hardware and software) opens door to various real-world security threats.
SIDE CHANNEL ATTACKS
Over the past few decades, new forms of attacks are constantly introduced where the hacker observes and
analyses the side-channel (channel through which information leaks) information in order to recover the
secret keys. In fact, software and hardware implementation of these devices leak sensitive correlated information in the
form of power consumption, time required for execution, electromagnetic emission, allowing hackers a good scope
to recover the secret keys with considerable accuracy. These types of attacks are called “side-channel attacks”.
POWER SIDE CHANNEL ANALYSIS
In this work, we explored the power-side channel analysis as case study. These attacks, usually involve
demonstrating the relationship between the data being manipulated by the cryptographic device and theinstantaneous power consumed.
Simple power analysis (SPA), differential power analysis (DPA), and correlation power analysis (CPA) are three
fundamental techniques of power-based side channel attacks. The SPA attack is applicable when the leak is so
evident that simple analysis techniques such as visual inspection can disclose the secret information, however the
DPA method employs statistical analysis using many power measurements. This work studies the power-based side
channel analysis and precisely CPA attack. The CPA analysis uses a set of power measurements of a
cryptographic device under attack in order to reveal thesecret information by exploiting the correlation with the
internal data or internal operations. Indeed, the measured power traces have different statistical distributions that can
be exploited because it depends on the operands or the operations. A hacker can reveal secret information by
analysing these distributions.
CHIP WHISPERER
ChipWhisperer is a complete opensource toolchain for learning about side channel attacks on embedded devices
and validating the side channel resistance of these devices. In particular, ChipWhisperer focuses on power analysis,
which uses information leaked by a device’s power consumption to mount an attack, as well as voltage and
clock glitching attacks, which briefly disrupt a device’s power or clock to cause unintended behavior (such as
skipping a password check).
COMPONENTS
In total, ChipWhisperer has few layers of opensource components as mentioned below:
a.Hardware
ChipWhisperer has scope boards, which are used to mount side channel attacks, as well as target boards,
which function as a device under test.
b.Firmware
ChipWhisperer also includes opensource firmware for both scopes and targets. Scope firmware is written in
Verilog (for the FPGA) and C (USB microcontroller).
c.software
ChipWhisperer has an opensource Python library for controlling the capture hardware and communicating
with the target.
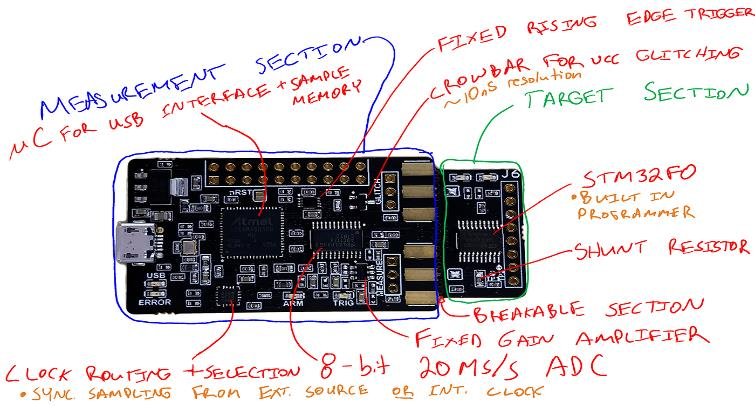
Figure 1: Chipwhisperer nano board
ADVANCED ENCRYPTION STANDARD
The AES is a symmetric block cipher and round-based encryption algorithm where the number of rounds
depends on the key length: 14 rounds for 256-bit keys,12 rounds for 192-bit keys and 10 rounds for 128-bit
keys. The AES algorithm takes a block with 128 bit lengths and every data block consists of 4 x 4 array of
bytes called the state.
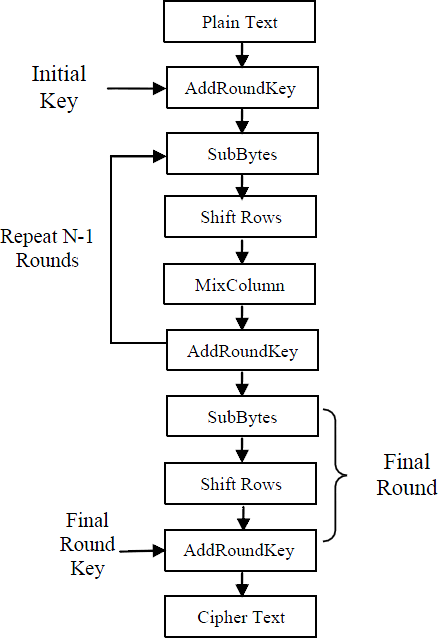
Figure2: Simplified block diagram of AES
AES IMPLEMENTATION:
The AES algorithm may be implemented software or hardware. In this case study, we have implemented AES in software.
CPA HACKING TECHNIQUE
The simulated CPA attack, against AES algorithm, uses asimulated power measurement. To perform this step, we
used 100 random AES plain-text and one fixed secret 128-key. These simulated power-measurements are saved in a
matrix denoted S.
Secondly, the power consumption of the target 128-AES implementation is predicted using 256 sub-key
assumptions. In this simulated attack, we used the initial s-box output as a target point attack. The predicted power
consumption calculated by the power model depends on corresponding secret sub-key assumption ranges from 0 to
255 and the plaintext.
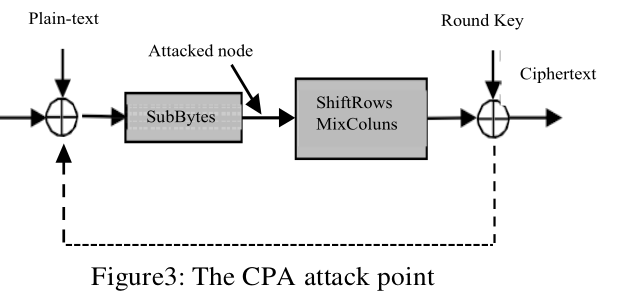
In fact, the initial AES round of AES begins by the RoundKey transformation followed by the Subbytes
transformation. The Subbytes transformation divides the 128- bit RoundKey output [128-key ⊕ 128-bit plain-texts] into 16
substitution boxes (S-box). Every S-box receipts one byte at input and products one byte at output. Consequently, the
assumption of one byte of the key (sub-key) is easy to calculate.
Therefore, using the same AES inputs of the simulated power measurements, we compute predicted power
consumption of the target point attack for 256 sub-key guess (256 assumptions: 28). While the AES-128bits is used as a
case study, this step is repeated 16 times because it must be performed for the 16 S-box. At the end, we obtain a predicted
power matrix of size N x 256 x 16.
In this step, the Hamming weight model is used where suppose that the point attack is equal zero at the initial
moment. Finally, to reveal the secret key, we compute the correlation coefficients between the predicted power
consumption and the simulated power consumption. The highest correlation value corresponds to the first byte of the
correct key while the correlation coefficient corresponding to the incorrect sub-key assumption remain low.
CPA AGAINST SOFTWARE AES
Correlation power analysis is done in order to retrieve the secret key. In this section, CPA based side-channel attacks
against software implemented AES is demonstrated.
Here, N plain texts and their corresponding power traces are exploited. At first, we estimate the AES implementation
power consumption by the hamming weight power model(one of the leakage models). The attack point chosen is the
output of the s-box (subbyte step) after the first round.
Finally, we calculate the correlation factor, by measuring thesimilarity between the real power measurements and the
predicted power consumption for all the possible 256 sub-key guesses.
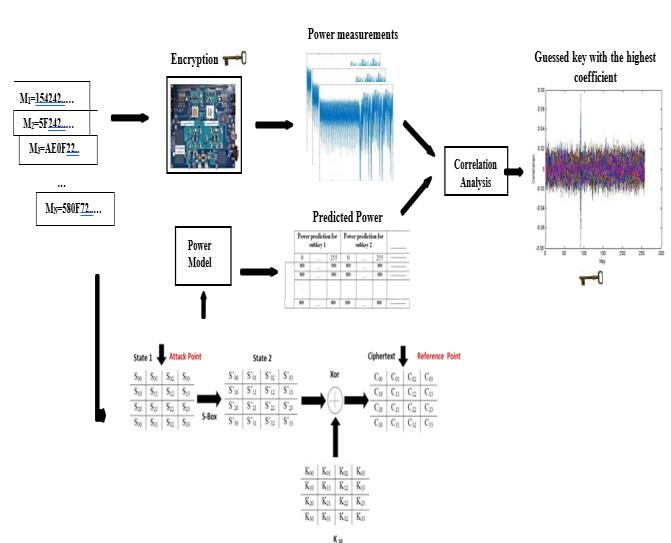
Figure4: CPA against AES
It is observed that, a unique correlation value corresponding to the correct sub-key assumption has the
highest correlation value. Even, the correct key assumption stands out with a notable difference leading tosure verdict of successful attack.
RESULTS:
It is observed that the correlation between the correct sub-key assumption and the power measurements is close to 1.
Therefore, we can assume that these CPA hacking techniques against microcontroller-based software implementation can break the security of the cryptographic
device by revealing secret information like secret key.Also, hamming weight used as case study in this attack
proves its effectiveness to predict device power consumption.
Secret Key:
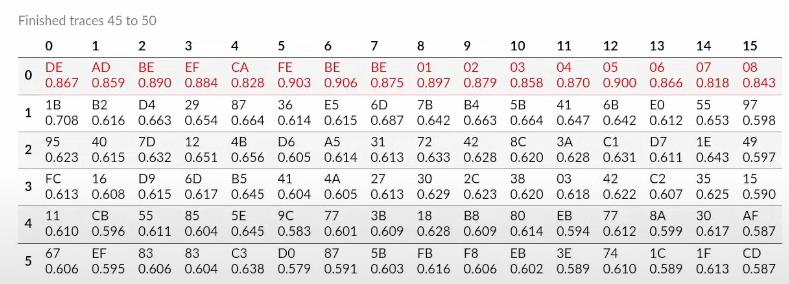
Figure5: Broken secret key of AES using CPA and ChipWhisperer Nano,”
REASONS FOR FAILURE OF AES
Though AES is trusted encryption algorithm, our study
showed there is quite high possibility of secret informationleakage. And this can be because:
1. The algorithm is implemented in such a way thatit creates distinctive power consumption patterns
depending on the processing data. For example,certain operations in AES like s-box substitution
and key addition, have unique power consumption,that can be detected and analysed.
2.
AES algorithm uses symmetric encryption keys where in same key is used both for encryption and
decryption So, there is quite security issue.
CONCLUSION
Power based side channel attacks became a realistic threat for both hardware and software implementations of the
cryptographic algorithms. In this project, we explained how power analysis can be exploited to reveal secret key by using
powerful CPA attack.
REFERENCE
1. Advanced Encryption
Standard: https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
2. Correlation Power
Analysis: https://wiki.newae.com/Correlation_Power_
3. ChipWhisperer-
Nano: https://rtfm.newae.com/Capture/ChipWhisperer-Nano
4. ChipWhisperer
Documentation: https://chipwhisperer.readthedocs.io/en/latest
5. ChipWhisperer Jupyter
Notebooks: https://github.com/newaetech/chipwhisper er-jupyter
6. L. Lathrop, “Differential Power Analysis Attacks on
Different Implementations of AES
Code: code part
Demo:Power side-channel attack on software implemented AES
Recent Comments